It uses policy-enforced, transparent encryption to prevent unauthorized access to your information across removable media, network servers, and computer hard drives. The software is available for Microsoft Windows tablets, laptops, desktop PCs and workstations, and Mac OS X endpoints. On the next window that opens, enter the name of your desired folder to be created on the removable media. This will be used by the File Encryption client to encrypt the content. After setting the policy that you want, click OK. You will now see the folder that you have entered.
Enterprises seeking a way to encrypt their growing number of Macintosh devices now have a new option from PGP. The company has unveiled a Mac OS X version of its Whole Disk Encryption 9.9 security software.
As with its Windows counterpart, the Macintosh version has been validated for use by the U.S. government to protect data on laptops, desktops and portable media devices.
Unlike other encryption solutions, both versions come with a preboot authentication check.
'This lets IT manage those Macs that are now side by side with PCs,' John Dasher, PGP's director of product management, told InternetNews.com.
Macintosh platform security is a growing concern as the Mac OS X gains traction in enterprise infrastructure. Dasher said Macintosh products are often overlooked when it comes to security, as Windows has been dominant in most businesses.
He recounted an incident this past February at the National Institute of Health (NIH) in which a laptop theft exposed confidential clinical information on 2,500 patients.
The data was housed on both Windows and Mac devices, but the Macintosh computers were not encrypted, he explained. In response the NIH now prohibits Mac laptops for use when dealing with sensitive data, Dasher said.
Enterprise adoption of Macintosh products tripled last year to 4.2 percent, according to a Forrester Research (NASDAQ: FORR) report this past March.
The Yankee Group reported that 87 percent of companies now have some Macintosh computers plugged in -- a spike of 48 percent over two years.
Those numbers will continue to rise given the popularity of new laptops such as the MacBook Air. IDC (NYSE: IDC) reported that laptops will constitute 68 percent of all computers by 2011 as they increasingly replace desktops.
Security risks will increase in tandem given research indicates many data breaches involve portable devices and malware writers are now aiming for the platform as well. According to Ponemon Institute, 56 percent of mobile data breaches are due to lost devices including laptops and removable media.
In February security vendor Sophos reported that financially motivated hackers had targeted Apple Mac computers with malware for the first time.
The average cost of a breach is $197, an increase of 43 percent since 2005, according to Ponemon.
'Macs are slowly gaining ground, but since management vendors have focused on Windows, there is a security and an operations gap,' Jon Oltsik, senior analyst for information security at Enterprise Strategy Group, told InternetNews.com. 'PGP recognizes this and is responding with product support. I expect lots of others [security vendors] to follow,' Oltsik said.
Whole Disk Encryption secures all the contents of a laptop, desktop, external drive and flash drive, from boot sectors to system files. When tech teams use the software with the PGP Universal Server, they can manage policies, users, keys and configurations from a single console.
Removable Media Encryption For Mac Not Report To See Server Settings
'This is a very transparent full-disk encryption approach that goes from the hard drive to the thumb device for complete protection,' said Dasher, adding that it's 'defense in depth as the best security is achieved with layers.'
The product will be available in July. Pricing is $119 per user for the stand-alone version, and when the software is used with the PGP Universal Management Server, the annual subscription for 1,000 seats is $42,000. A perpetual license is $104,000.
UC Berkeley security policy mandates compliance with Minimum Security Standard for Electronic Information for devices handling covered data. The recommendations below are provided as optional guidance to assist with achieving the Data Encryption on Removable Media requirement.
Requirement
Anyone storing covered data on portable devices (such as laptops and smartphones) or removable and easily transported storage media (such as USB drives or CDs/DVDs) must use industry-accepted encryption technologies.
Description of Risk
Malicious users may gain unauthorized physical or logical access to a device, transfer information from the device to an attacker’s system, and perform other actions that jeopardize the confidentiality of the information on a device.
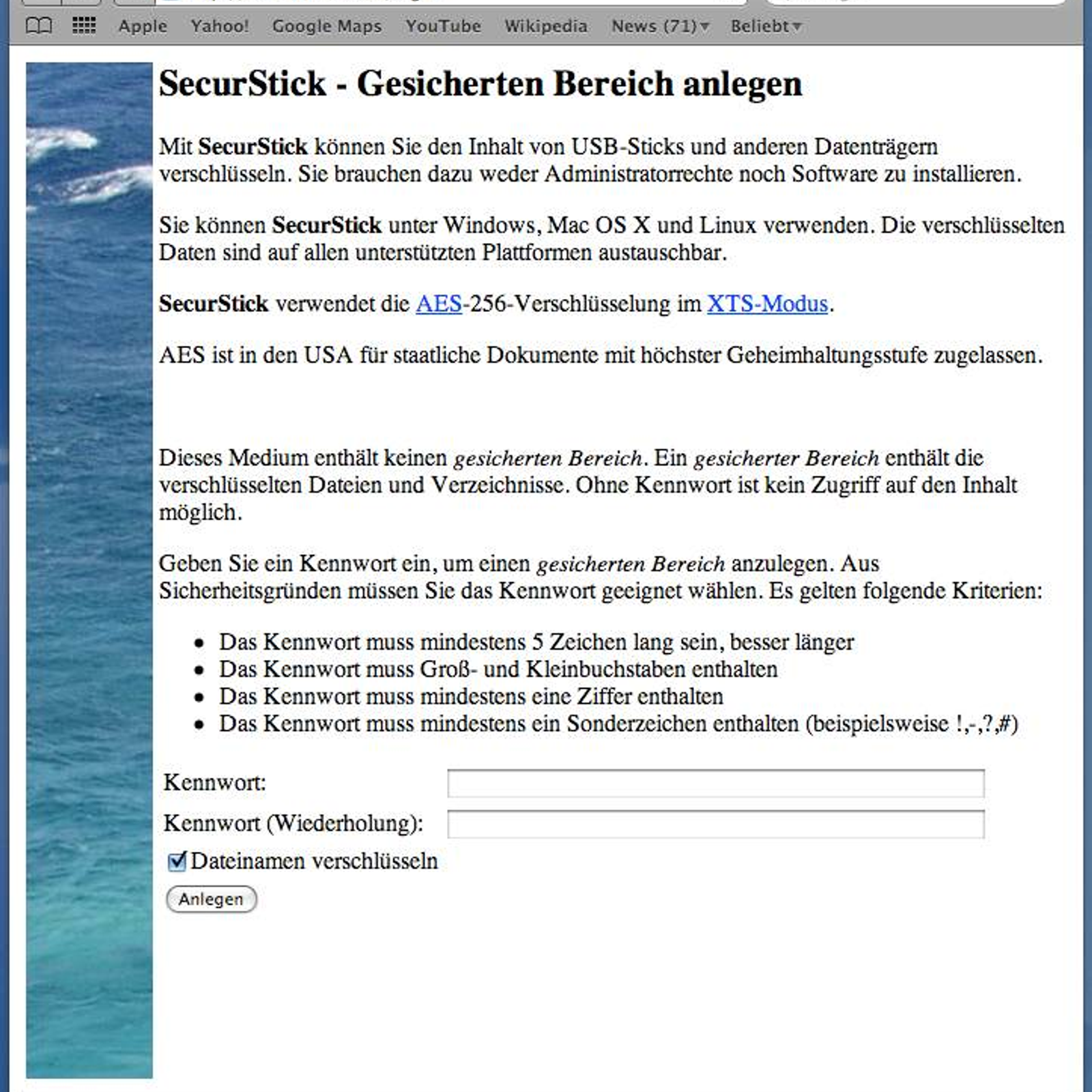
Recommendations
Removable media and mobile devices must be properly encrypted following the guidelines below when used to store covered data. Mobile devices include laptops and smartphones.
- Develop and test an appropriate Data Recovery Plan (see Additional Resources)
- Use compliant encryption algorithms and tools
- Whenever possible, use AES (Advanced Encryption Standard) for the encryption algorithm because of its strength and speed. For more information, refer to NIST's Guide to Storage Encryption Technologies For End User Devices
- When creating a password, follow strong password requirements as defined in MSSND Control #5. Do NOT use the same password from other systems.
- Use a secure password management tool (see Additional Resources) to store sensitive information such as passwords and recovery keys
- Where passwords need to be shared with other users, ensure that passwords are sent separately from the encrypted file. E.g. call the person to verbally communicate the password.
- Do NOT write down the password and store it at the same location as the storage media (e.g. post-it note with the password next to the encrypted USB drive)
- After covered data is copied to removable media (e.g. CD, external hard drives):
- Verify that the removable media works by following instructions to read the encrypted covered data
- If applicable, securely delete unencrypted covered data following secure deletion guidelines
- Removable media should be labeled with the following information:
- Title. For example 'Project XYZ Data'
- Data owner (researcher or research unit name)
- Encryption date
- When unattended, the removable media should be stored in a secured and locked location (e.g. cabinets, lock boxes, etc.) where access is limited to users on a need-to-know basis.
- Document the physical location of removable media, along with the label information (specified above) for tracking and future reference.
Compliant Encryption Tools
The various tools for encrypting data can be divided into 3 broad categories: 1) Self Encrypting USB Drives, 2) Media Encryption Software, 3) File Encryption Software.
Self Encrypting USB Drives are portable USB drives that embed encryption algorithms within the hard drive, thus eliminating the need to install any encryption software. The limitation of such devices is that the files are only encrypted when residing on the encrypted USB drive, which means files copied from the USB drive to be sent over email or other file sharing options will not protected. These USB drives are also typically more expensive than non-encrypting USB drives.
Full Disk Encryption Software is software that is used to encrypt otherwise unprotected storage media such as CDs, DVDs, USB drives or laptop hard drives. The flexibility of this software allows protection to be applied to a greater selection of storage media. However, the same limitation on collaboration applies to media encryption software as it does to Self Encrypting USB Drives.
File Encryption Software allows greater flexibility in applying encryption to specific files. When using File Encryption Software properly, resource proprietors can share encrypted files over email or other file sharing mechanisms while maintaining protection. To share encrypted files, ensure that passwords are shared securely following recommendation 4.a above.
Below is a sample list of tools that comply with removable media encryption requirements:
| Tool Category | Tool Options | Best For |
|---|---|---|
| Self-Encrypting USB Drives |
| |
| Full Disk Encryption Software |
|
|
| File Encryption Software |
|
|
The tools listed generally support modern operating systems such as Microsoft Windows, Mac OS X and Linux. Please consult vendor websites for specific system requirements.
Non-Compliant Encryption Tools
Many software applications provide password protections features that only provide a veil of security which is trivial to defeat. Software which does not meet encryption standards includes:
- Adobe Acrobat prior to version 10.0 (a.k.a. version X)
- Microsoft Office application prior to 2010
- Winzip prior to version 9
In addition to following the provided recommendations, use tools mentioned in the Compliant Tools section whenever possible. If you are uncertain about an encryption tool, please contact security@berkeley.edu for consultation.
Additional Resources
Removable Media Encryption For Mac Not Report To See Server Permissions
Data Recovery Plan
If removable media is the sole copy of covered data, you should do the following to ensure covered data is securely backed-up to other devices.
- Covered data is backed-up to other removable media that adhere to the requirements set forth in this document or
- Covered data is backed-up to UCBackup with encryption
Password Management Tool
Removable Media Encryption For Mac Not Report To See Server Ip
A password management tool is a solution that allows use of a single complex master password to protect all your other passwords and credentials in a central location. It also reduces the need for users to remember all the username and password permutations used for various application and web services.
Removable Media Encryption For Mac Not Report To See Server Instance
While convenient, the breadth of access provided by a password management tool requires heightened security to protect the password management database. Here are some recommendations on how to prevent your password management database from falling into the wrong hands:
Do NOT share the password management database on websites or file sharing services
Follow good password practices when creating the master password (meet MSSND #5 requirements AND be at least 10 characters long)
Regularly backup the password management database file to prevent being locked out of all your passwords.
Enable Multi-Factor Authentication (MFA) if the password management tool supports it.. The following MFA options should be favored over any SMS-based (text message) or phone-based MFA options as those are more susceptible to being bypassed.
Time-based OTP apps like Google Authenticator, Authy, or Duo
Physical U2F security key such as YubiKey
An example of password management tool is LastPass(link is external), which is available for free on Windows, Linux and Mac OS X operating systems.
